Passwords are no longer enough to secure corporate information technology (IT) networks and customer accounts, especially in the financial services sector. A NordPass survey found that the top 20 passwords used by Americans would take less than one second to crack. Many people also reuse passwords across multiple accounts — a sign of poor password management practices.
That’s why many organizations are turning to multifactor authentication (MFA) to secure their systems and data. MFA requires users to confirm their identity in two or more ways before gaining access. In this guide, we’ll explain what MFA is, how it works and why it’s a critical tool for your business.
What is multifactor authentication (MFA)?
MFA is a security measure that requires users to confirm their identity in two or more ways before accessing an account, system or building.
“Think of MFA as your digital bodyguard,” explained Scott Algeier, executive director of IT-ISAC. “MFA acts as an extra layer of security protection by creating additional obstacles for bad actors before they can access your system.”
For example, let’s say a hacker gets hold of an employee’s username and password. Without MFA, they could easily access your system. But with MFA in place, the hacker would need to get past a second — and sometimes a third — barrier, such as entering a unique code sent to the employee’s phone or generated by an authenticator app.
MFA can also apply to physical security. To unlock a secure door, someone might need to know a PIN, enter it on a keypad and then present a physical token, like a registered key card, to a reader.
With MFA, every additional factor creates another layer of defense — making it significantly harder for unauthorized users to break through.
How does MFA work?
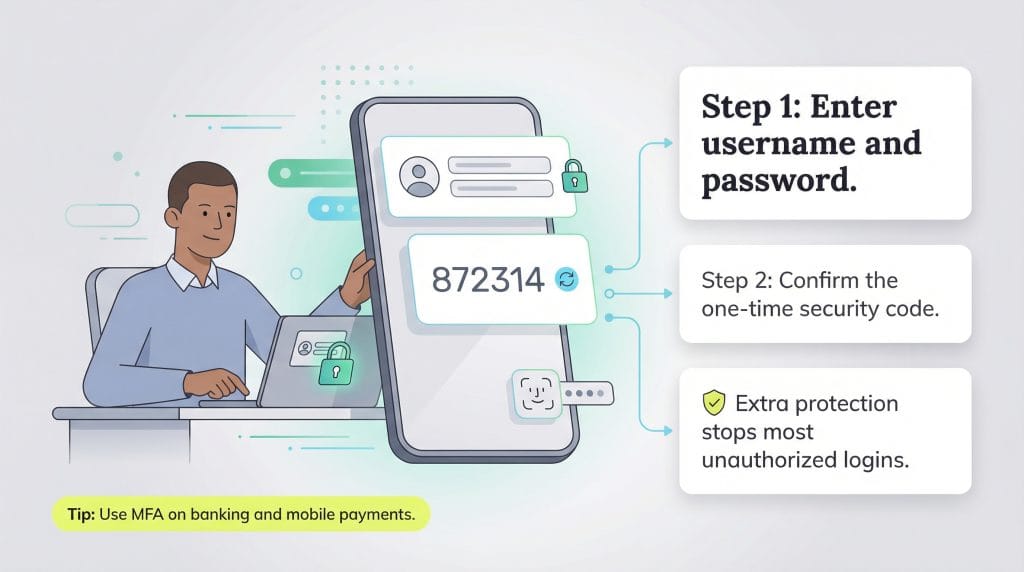
MFA requires users to pass at least two identity checks before gaining access to online accounts or IT systems.
For example, banks often use MFA to protect their customers’ money. Here’s how it works:
- The customer enters their username and password on the bank’s website or app.
- The bank sends an authentication code to the customer’s phone via text message, push notification or an authenticator app.
- The customer enters the code to verify their identity and access the account. If the wrong code is entered, access is denied. After multiple failed attempts, the bank may block further login attempts.
Mobile wallets often use elements of MFA. For example, unlocking the wallet with facial recognition and then verifying a purchase with a passcode or linked device can provide two layers of protection.
Even with robust MFA practices, cybercriminals may be able to access data. Consider getting
cyber insurance to help manage the financial fallout from a potential data breach.
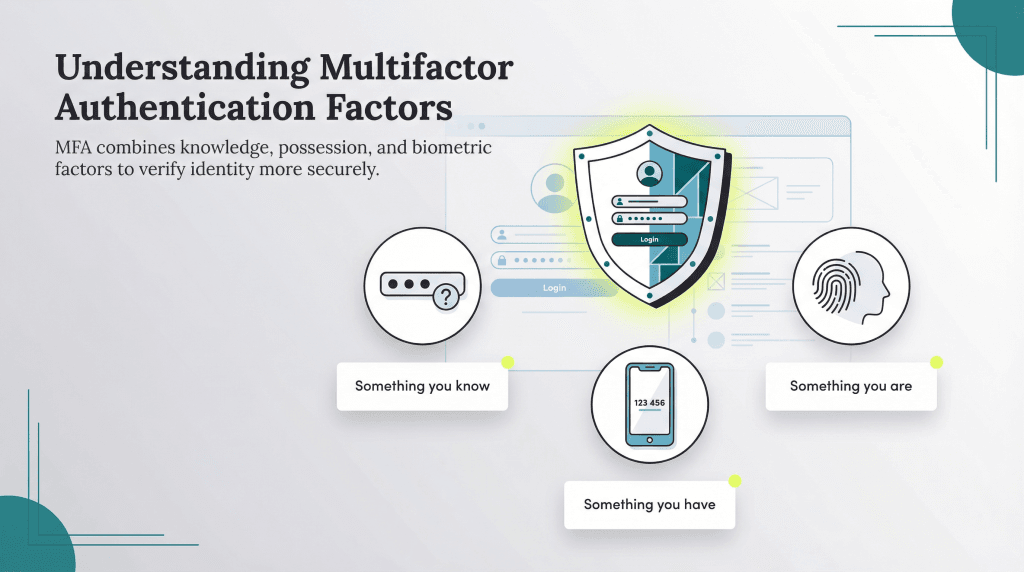
Types of authentication factors
MFA systems verify your identity using three criteria:
- Something you know
- Something you have
- Something you are
Something you know
“Something you know,” also called a knowledge factor, refers to information that only the user should be able to recall.
Common knowledge factors include passwords, PINs and answers to security questions like your mother’s maiden name or your pet’s first name.
However, knowledge factors come with two major security weaknesses:
- Weak passwords: Many people reuse passwords or create ones that are easy to guess.
- Personal details: Passwords and passcodes often include personal information — such as a child’s name or birthday — that attackers can discover easily. Spear phishing attackers often research their targets in advance to guess these details and gain access.
Because of these risks, MFA methods always combine a password with at least one other authentication factor. Some vendors are even working to phase out knowledge factors entirely.
Something you have
“Something you have,” also known as possession factor authentication, refers to a physical item the user must have in their possession to verify their identity. Common examples include:
- A mobile device that receives authentication codes via push notification, text message or an authenticator app
- A hardware security key, like a YubiKey or USB stick
- A smart card or ID badge used as a hardware fob
Possession-based factors boost security because, even if a hacker obtains someone’s password, they’d still need physical access to the second device to complete the login process. Since devices can be lost or stolen, most MFA solutions make it easy to deactivate a compromised key, fob or USB stick and register a replacement. If someone loses their phone, you can simply deregister it and activate a new one.
Many security experts recommend codes sent through authenticator apps or hardware keys over short message service (SMS)-based authentication. “SMS messages can be intercepted or hijacked through SIM swapping and phone-number porting attacks — making them less secure than app- or hardware-based options,” cautioned Josh Summers, founder of All Things Secured.
Dave Hatter, a cybersecurity consultant at Intrust IT, agreed. “A hardware key like a YubiKey is typically more secure than an MFA app like Authy, which in turn is generally more secure than an SMS-based code,” Hatter explained. “Man-in-the-middle cyberattacks can defeat some non-phish-resistant MFA, so phish-resistant methods are increasingly the recommended approach. Ultimately, though, any MFA is far better than none.”
When performing a
cybersecurity risk assessment, consider implementing an MFA solution as part of your strategy. It's one of the most effective ways to mitigate the risk of unauthorized access.
Something you are
“Something you are,” also known as an inherence factor, refers to biometric or physical attributes that are unique to you, such as:
- Fingerprints
- Face, retinal and iris features
- Voice patterns
Biometric authentication is often the hardest authentication factor to bypass. Your face, fingerprint or iris is always with you — and these identifiers are very difficult to fake, share or forget. When you log into an app using your fingerprint, the system can be confident it’s really you.
Many smartphones already include biometric authentication, such as facial recognition or fingerprint scanning. However, for physical access, such as unlocking doors, you may need specialized hardware, such as a fingerprint reader or a security camera with infrared capabilities for facial recognition.
Start using an MFA
MFA can be tailored to different business needs and risk levels, from remote access to high-security environments. The best MFA system for your business depends on what you’re protecting and how secure it needs to be. Here are some examples:
- Remote workforce: If you have a remote work plan, offsite employees must access your cloud-based apps. In these cases, MFA typically includes a password (something you know) as the first factor and a passcode sent to the user’s mobile device (something you have) as the second factor.
- Entry to premises: To prevent unauthorized access to your physical location, the most robust setup is a three-factor MFA system: A physical token to swipe (something you have), a PIN code to enter (something you know) and a biometric scan (something you are).
- Financial transactions: Many banks use biometric verification (something you are), such as fingerprint or facial recognition, either alone or combined with a one-time code sent to a device you possess (something you have).
Another option is adaptive MFA, which uses artificial intelligence and machine learning to monitor user activity and behavior and determine, case by case, which identity verification steps are needed for a given login. For low-risk logins — like an employee signing into the corporate network from a recognized device — an adaptive authentication system may decide that a password is sufficient. However, the system can adapt. For example:
- If the login comes from an unrecognized device, it may prompt for a second form of verification.
- If someone attempts to log in from an unfamiliar device in another country, the system might require a third authentication step before granting access.
However, even with risk-based authentication, companies must remain vigilant, according to Blair Cohen, founder and president of AuthenticID. “Bad actors’ tactics continue to evolve and companies must continuously strengthen protocols,” Cohen cautioned. “To address these challenges more effectively, many organizations are turning toward passwordless authentication, such as biometrics and token-based solutions, which offer a more seamless and resilient defense.”
In other words, attackers are getting smarter. Companies should pair risk-based MFA with broader improvements — including moving beyond passwords — to help prevent data breaches and network intrusions.
It's important to choose an MFA solution with an easy account recovery process. Otherwise, you risk unnecessary downtime and frustration for legitimate users.
To start using MFA in your business, follow these steps:
- Prioritize security: MFA isn’t expensive, but leadership buy-in is essential for a successful rollout. “Trying to sell and implement security awareness modernization from the ground up is a difficult task that will almost certainly fail,” warned Steve Tcherchian, chief information security officer and chief product officer at cybersecurity solutions company XYPRO.com. “This is simplified if the company regards employee security awareness as a business risk.” In other words, frame MFA as a way to protect your business’s sensitive information and ensure continuity — not just a cost-saving measure.
- Identify areas with a pressing need for MFA: Start with the systems that pose the highest risk. MFA should be implemented for employees who handle sensitive data, as well as executives vulnerable to spear-phishing attacks. Be sure your MFA system covers any regulatory requirements, such as Payment Card Industry Data Security Standard, Sarbanes-Oxley Act or Health Insurance Portability and Accountability Act laws.
- Select an MFA solution: Research the best MFA apps and speak with vendors to explain your goals. Ask for their recommendations on the simplest, most effective setup for your needs. Always request a free trial or demo to test the platform’s usability — the more intuitive it is, the faster employees will adopt it. “Simpler is often better,” noted Joe Warnimont, senior analyst at HostingAdvice. “Finding a tool that’s somewhat familiar to your workforce … is far more important than a tool that’s cheap or has all the best MFA features.”
- Roll it out in stages: Launch your MFA system in phases, starting with a test group or employees who present the highest risk. For higher-risk activities — like logins from unknown devices or locations — select MFA methods that offer the right level of protection. For everyone, aim to balance security with usability so MFA doesn’t become a barrier to daily work.
- Train your team: Invest in employee training to ensure everyone is comfortable using MFA. Keep instructions clear, accessible and easy to complete. Help employees understand why MFA matters by tying it back to protecting data and the business. Workflow automation and gamification can boost engagement, according to Tcherchian. “You can set it and forget it with security awareness automation, eliminating the need for missed training or manual effort,” Tcherchian noted. “People can be organized into teams and the experience can be gamified. When there is healthy competition, everyone is involved in the process.”
- Monitor for effectiveness: Evaluate how well your pilot group adapts to the new MFA system. Gather feedback, track any security issues and tweak as needed before scaling to the whole company. Have backup procedures in place for lost or stolen devices. Review your MFA policies regularly and update them if new threats arise or regulations change.
MFA vs. 2FA
2FA — two-factor authentication, also called two-step authentication — is a specific type of MFA that requires users to verify their identity using two authentication factors. For example, the first step may involve entering a username and password, while the second may involve entering a code sent to the user’s mobile device.
In contrast, MFA systems require two or more verification steps — potentially even three or more factors for higher-risk environments. MFA is a broader category that offers more flexibility and stronger security for businesses that need additional protection.
For many businesses, 2FA offers a solid balance between security, usability and ease of access. However, MFA provides an extra layer of defense for organizations handling sensitive data or operating in high-risk sectors.
To enable MFA quickly — and for free — start with Google Authenticator or Microsoft Authenticator. For more advanced access control, consider paid options like NordPass Business or Okta Verify, which cost just a few dollars per user per month.
Should I use MFA for my business?
Yes, you should use MFA for your business. Here’s why:
- Reduced cybersecurity risk: MFA lowers cybersecurity risks. Even if hackers obtain a password, MFA blocks them from accessing your systems without a second verification factor.
- Better protection for small and midsize businesses (SMBs): While big business cyberattacks make headlines, SMBs are often targeted because they lack strong cybersecurity. MFA is an affordable, easy-to-use solution that helps protect businesses of all sizes.
- Improved regulatory compliance: Many regulatory bodies and insurance providers now expect businesses to implement MFA — especially those that handle sensitive or personal data.
- Stronger financial protection: The cost of MFA is minor compared to the potential financial damage of a data breach. “Organizations that implemented MFA saved an average of $460,000 per incident and discovered the breach 108 days faster,” said Kiran Chinnagangannagari, co-founder and chief product & technology officer at Securin.
Businesses face significant risks if they don’t have MFA-based access management in place to block unauthorized access to their networks or physical premises. “Delaying adoption of robust authentication is no longer an option,” Chinnagangannagari cautioned. “The question is not whether to implement MFA, but how quickly you can roll it out effectively.”