Your sensitive customer data and intellectual property are under constant threat from cyber attackers. If they successfully manage to download their malware onto your IT network, they could shut it down and stop you from doing business. If your sensitive data were to get into the wrong hands, the financial and reputational damage to your firm could be disastrous. There’s never been a more important time to invest in cybersecurity for business.
Below, find out how to do a cybersecurity risk assessment to discover your firm’s vulnerabilities and why it makes business sense to tighten up your defenses.
How to do a cybersecurity risk assessment
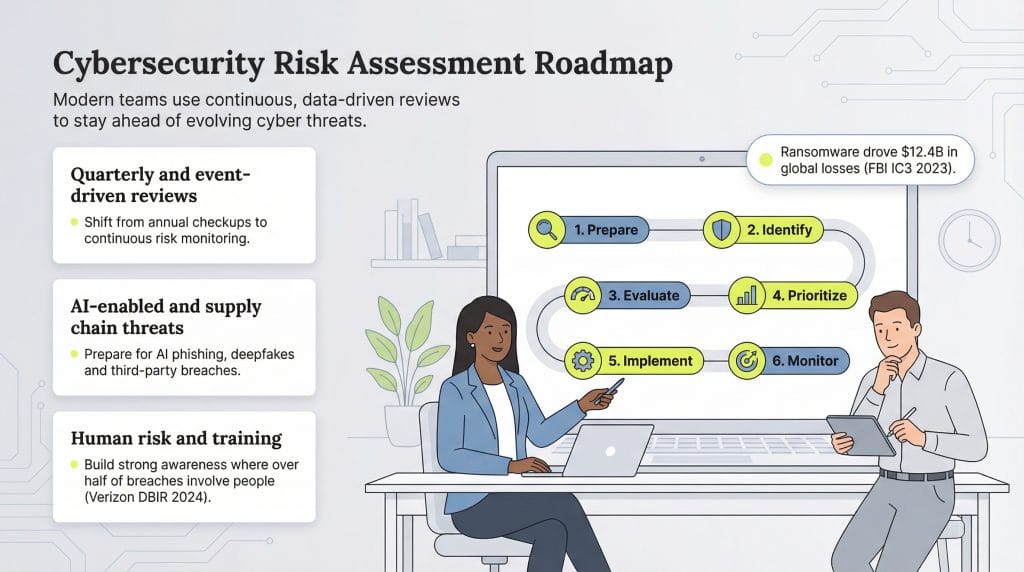
Cybersecurity threats constantly evolve as hackers find new ways to break into companies’ IT networks. Experts recommend that businesses carry out risk assessments quarterly or bi-annually — at the very least annually — with additional assessments following any major system changes or security incidents as part of their overall cybersecurity plan.
Take the following steps to carry out a cybersecurity risk assessment.
1. Research and prepare.
To understand the technical weaknesses in your IT network, you need in-depth knowledge of how your systems and devices connect with each other and the outside world. Follow these steps as part of your preparation:
Map your digital ecosystem.
Start by listing all the hardware, software and online apps — like accounting software and customer relationship management (CRM) systems — that you use in your business. Keep handy key documentation on each item of equipment or app you’re using, together with details such as vendor information, update and version histories, and who within the business is responsible for maintaining or managing it.
Gather information about your devices.
Compile the same information on each device or program that connects to your network and to the internet. These devices include your Wi-Fi routers, printers and security cameras. Also list the apps that talk to other apps via plug-ins or application programming interfaces, because they can send, modify and receive company data. [Read related article: How to Set up Wi-Fi for Your Business]
List all users.
Determine who has access to your network, data, software and apps. Be sure to include freelancers, software providers, partners, vendors and other third parties, if applicable. List the people who are responsible for granting and denying access to employees and outsiders, as well as those in charge of configuring your network. If your business has an e-commerce presence, find out how well they protect your online store from attack, particularly if it connects to your internal software.
Assess your current recovery plan.
Examine your current plans for recovering data and access to your systems in the event of a cyber breach.
After following these steps, you’ll have a clear understanding of what and who are on your network and how they interact with each other. If you don’t feel confident about doing this and you have no in-house IT people, you can call in a cybersecurity expert to conduct this part of your assessment.
In cybersecurity management, recordkeeping is essential. The detailed documentation you create at all stages of this process helps you understand the configuration of your tech setup and the true state of your current security.
2. Identify assets, threats, vulnerabilities and regulatory requirements.
The next step is to find out what needs to be protected and the types of attack you need to prevent. Here’s how to do it:
Identify your valuable assets.
As a business, you’ll create and accumulate more data every day. Some data is particularly important, like your customer information, financial records and any unique intellectual property your company owns. [Read related article: 17 Security Tips to Protect Your Business’s Information]
Most valuable is the data that, if lost or unaccessible, would cause a substantial operational hit to your business, either to your finances or your reputation. Your customers may switch to a competitor if they believe you can’t protect their sensitive data.
Your technology — including hardware, software and apps — is valuable, too. For example, getting locked out of your central server or allowing hackers to download key data from your CRM system could be catastrophic. This is a common tactic used in ransomware and cyber extortion attacks. According to the FBI’s Internet Crime Report ransomware attacks cost businesses over $12.4 billion.
Remember that the data you hold in the cloud is just as important as the data you hold on-site. [Read related article: SMB Guide to the Different Cloud Services]
Make a comprehensive list of the minimum assets you need to operate as a business. This will help you decide where to focus the bulk of your cybersecurity efforts and resources.
WPA3-Enterprise is considered the gold standard networking protocol for wireless security.
Identify threats.
The nature of the threats presented by cybercriminals changes constantly. In 2026, businesses should watch for AI-powered attacks, supply chain vulnerabilities and sophisticated social engineering campaigns that use deepfake technology. The following resources are useful for staying informed of the latest risks and how to prepare and respond to them:
- The MITRE ATT&CK knowledge base: This comprehensive resource catalogs common attack techniques and provides a framework for understanding threat behaviors.
- Cyber Threat Alliance: The Cyber Threat Alliance provides up-to-date cyber-threat information that it receives directly from some of the world’s leading security companies.
- Security vendor reports: Leading cybersecurity companies like CrowdStrike, Palo Alto Networks and Microsoft publish regular threat intelligence reports highlighting emerging risks and attack patterns.
- Government resources: The Cybersecurity & Infrastructure Security Agency and other government entities provide alerts on threats targeting specific industries, regions or technologies. The FBI’s Internet Crime Complaint Center, Britain’s National Cyber Security Centre and the National Institute for Standards and Technology’s National Vulnerability Database are also excellent resources.
- Lockheed Martin Cyber Kill Chain: This model shows the stages of a typical cyberattack, from when hackers are doing their initial research until the data breach. If your assessment highlights your email system as being vulnerable to your cyber defenses at the delivery stage, you can prioritize your email system security in response — for example, by installing stronger spam filters or training staff members on scams that target small businesses, like phishing emails.
- News sites: Bookmark CyWare Social, Security Week and The Hacker News for news and reports on data breaches and cyberattacks.
E-commerce website security best practices include working with a secure e-commerce platform, staying on top of SSL certificates and using a virtual private network (VPN).
Identify vulnerabilities.
Now that you know the most likely threats to your core business assets, you must identify your systems’ vulnerabilities. For example, potential attack vectors may result from outdated software, weak passwords, poorly configured systems and weak authentication mechanisms.
To test how vulnerable they are, you could run a configuration audit, a manual penetration test, an automated scan or a code review on any custom software you’re using. This will flag any existing weaknesses right away.
In addition, it’s important to invest in cybersecurity training for your staff. According to Verizon’s Data Breach Investigations Report, humans were an element in about 60 percent of all security beaches.
During the first stage of this process, you made a list of each piece of hardware, software or app and who was responsible for maintaining and managing them. You also listed who was responsible for granting and denying access to your systems. See what rules they’re operating by and whether they’re fulfilling their duties as required. Include your website in your assessment, too, if it connects to your CRM system or other internal apps.
In addition, consider what rules your general staff members are using. You may discover additional gaps in your security processes and procedures. If you already have a security policy in place, make sure people are adhering to it and their managers are enforcing it, because even the best security measures can be undermined by human error or negligence.
You should not overlook threats from internal actors, like disgruntled employees. The Association of Certified Fraud Examiners’ Report to the Nations found that organizations lose 5 percent of their revenue to occupational fraud, with the median loss reaching $145,000 per case. While it may be next to impossible for them to access your company’s checking account, someone may have eyes on your customer database and want to take it for themselves. [Read related article: How to Prevent Employee Accounting Fraud]
Review your access privilege management. Ensure that employees have access only to the systems and data necessary for their roles and that privileges are regularly reviewed and updated. As soon as an employee leaves the company, deny them access to your network.
Start and maintain a vulnerability inventory that you retain as part of your company’s internal cybersecurity documentation.
Consider investing in
cybersecurity insurance coverage, including data breach and cyber liability insurance, to insure against losses from data breaches, ransomware and other cybersecurity threats. To cover data theft from both nondigital records and digital records, you’ll need
data breach insurance.
Identify regulatory requirements.
A key element in any cybersecurity risk assessment should be verifying that you comply with all relevant regulatory requirements.
For example, if you’re in the health care sector in the U.S., you’ll need to comply with HIPAA. If you handle European Union citizens’ data, regardless of where your business is located, you’ll need to adhere to the General Data Protection Regulation. If you take debit or credit cards, you’ll need Payment Card Industry Data Security Standard clearance to comply with payment processing rules and laws. Additionally, as of 2024, several U.S. states including California, Virginia, Colorado and Connecticut have passed comprehensive data privacy laws that may impact your business depending on your revenue and data processing activities.
These frameworks share three features:
- You need to audit your systems.
- You need to focus on data protection.
- You need to notify authorities and affected parties in the event of a breach.
If you’re not sure of the regulations governing your business, you could hire an attorney with expertise in this area. Ask them to create a comprehensive list of the requirements you need to adhere to, paying special attention to any gaps in your existing security measures.
Because regulations change often, you may wish to pay a retainer to your lawyer to keep you advised of any new legislation or changes to existing legislation. They can then advise you on how to prepare your systems for any changes to the current regulatory landscape.
You can ask your lawyer to help you in all aspects of
cybersecurity and risk management. They can assist you during your cyber risk assessment, and that knowledge will be essential if you need to call upon them to manage the fallout from a breach.
3. Evaluate your risks.
The next step is to evaluate how likely your company is to fall victim to different types of attack and the impact this would have on your business.
Ask your IT lead or consultant to devise risk scenarios to determine the potential damage of an attack. Then, find out how to prevent these scenarios from happening and how you’d recover from one if it were to occur.
Consider the likelihood of each type of scenario. Many cybersecurity frameworks recommend using a rating system to do this. Think about how discoverable a vulnerability in your system is and how easy it could be exploited once found. Then, score each vulnerability on a scale from 1 (rare) to 5 (highly likely).
You can round these scores up or down depending on these factors:
- How capable your current security controls are in defending against a particular weakness
- How well your IT team could respond to and recover from an incident if it occurred
4. Prioritize your risks.
Now that you know which types of risk you’re most vulnerable to, the next step is to prioritize them so you can defend against the threats that are most likely to cause significant harm.
Many cybersecurity frameworks recommend prioritizing threats based on a five-factor matrix. You assign a score to each of five factors, sum them up and focus on the highest-scoring threats. These are the five factors to assess:
- Vulnerability: Using informational resources such as those mentioned earlier in this article, determine the likelihood of a particular threat.
- Business impact: Score threats 1 to 5 based on their potential business impact, with 1 meaning it would cause a minor inconvenience and 5 meaning it would involve catastrophic data loss or reputational damage.
- General awareness: Many cybercriminals target widely known vulnerabilities. That means you could award a lower score to less-known vulnerabilities because they’re less likely to occur.
- Skill required: Many IT experts would give a high score to easily exploitable weaknesses and a low score when a successful attack would require a highly skilled attacker with access to many resources.
- Patch availability: Vendors release patches for their software to protect against known vulnerabilities. If a patch is available, you should award a lower score; if not, award a higher score. [Read related article: Installing Windows Patches With PowerShell for Free]
For each high-priority risk you identify, you have three possible courses of action:
- Stop the activity that’s putting you at risk if the benefits don’t outweigh the risks
- Transfer the risk to a third party, like a cybersecurity consultancy, and mitigate the risk with cyber insurance
- Task someone with protecting the company against a breach, as well as introduce new internal security controls and/or purchase new hardware or software as required
While it’s impossible to eliminate all cyber risks, these steps should help your company successfully defend itself against the types of attack that could damage it the most.
5. Implement your cybersecurity strategy.
At this stage, you have a clear overview of how secure your data and IT network are, who can access both, how you handle sensitive data and the cyber threats you need to defend your company against.
Working with your senior team and outside consultants if needed, you should use this information to establish a plan that improves security across your business and prioritizes protection against the vulnerabilities that pose the greatest threat.
To implement your plan, build a team, assign clear responsibilities to each member and set deadlines for their tasks. Ask for regular progress reports, and if possible, allocate extra resources and personnel. Consider appointing a dedicated cybersecurity lead or virtual Chief Information Security Officer (vCISO) if your budget allows.
Remember to involve your general staff in the process as well, and begin training your employees on what they need to know as you implement the changes across your business. Pay attention to co-workers who don’t have strong technical knowledge, and make sure they understand what they’re being taught. You can also implement regular phishing simulations and security awareness training.
The best VPN services provide fast, secure connections while encrypting data. The intercepted data will be indecipherable even if a hacker infiltrates an employee’s device.
6. Document and report.
From initial planning to implementation and beyond, keep meticulous records of your cybersecurity strategy and why you made each decision. That way, if something goes wrong, you can show any external stakeholders and regulators the proactive actions you took to protect your network and data. In the event of a breach, no matter how minor, keep records of every action you took to manage it.
You should also review your policies regularly. Many experts now recommend continuous monitoring and quarterly reviews rather than annual assessments, particularly given the rapidly evolving threat landscape. Consider holding additional reviews in the aftermath of an attack or if there are major changes in your business, like adopting new technology or purchasing another business.