According to Cybersecurity Ventures, the global cost of cybercrime is expected to reach $10.5 trillion this year. So, shoring up cybersecurity vulnerabilities is a critical priority. One of the smartest steps a business can take is implementing multifactor authentication (MFA). MFA adds an extra hurdle for hackers to clear, helping keep your business safer. In fact, Microsoft reports that 99.9 percent of compromised accounts lack at least one additional verification step.
Authenticator apps are powerful MFA tools that generate one-time passcodes to boost account security and protect businesses from cybercrime. They add an extra layer of protection that users must pass through to access online accounts or company systems. We’ll explore six top-rated commercial authenticator apps to help you find the best option for your business. These tools are often part of broader identity management or MFA platforms, which may also be helpful for your organization.
Authenticator apps add a critical extra layer of security. If usernames and passwords are your only lines of defense, your business is a prime target for phishing and
ransomware attacks, malware, and other cybersecurity threats.
1. Twilio Authy
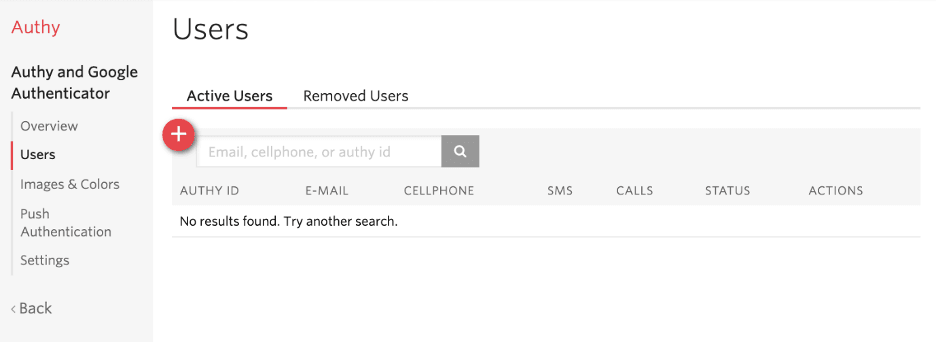
View active and removed users at any time through the Authy dashboard. Source: Twilio
Twilio Authy features and benefits
- Price: Starts at $0.05 per successful authentication, plus carrier fees if applicable. Volume discounts are available.
- Compatibility: iOS and Android mobile apps (including Apple Watch)
Businesses can deploy Twilio’s Authy authenticator app to secure employee logins and protect customers’ online accounts. Authy is part of Twilio’s broader suite of customizable services; it integrates seamlessly with its extensive range of communication tools and secure cloud backup.
Authy’s pay-as-you-go pricing makes it a smart choice for both SMBs and larger firms. For example, you’ll pay just $0.05 per successful authentication — around $2 per user, per month if employees log in daily during the workweek. That’s significantly less than many competitors.
It’s also ideal for e-commerce website security, as you can request authentication every time a user logs in from a new device. If you have a subscription website, you can request authentication whenever a user signs up or updates their bank details. At just $0.05 per authentication, the cost to your cybersecurity budget is marginal.
We also love Authy’s flexibility. You can choose your preferred verification methods and customize details like the length and validity of one-time codes.
- Multiple verification channels: Choose from text messages; voice calls; emails; push notifications; WhatsApp; time-based one-time passwords (TOTP); authenticator apps; QR codes; passkeys; and more.
- Silent Network Authentication: Verify phone numbers behind the scenes so users don’t need to enter a one-time password.
- International coverage: Twilio works in over 150 countries, making it suitable for global businesses.
- PSD2 compliance: Required for businesses selling to or accepting paid subscriptions from the European Union. [Read related article: How to Start a Membership Website]
- Developer-friendly platform: Ready-made libraries for Node.js, Python, PHP and more, with helpful code snippets to get coders started quickly.
- Scalable in pricing and capacity: Start small and pay per authentication, knowing Twilio can easily handle increased usage as you grow.
2. WatchGuard AuthPoint
WatchGuard regularly updates its AuthPoint software for different platforms. Source: WatchGuard
- Price: Charged per user at approximately $16 per year, per subscriber.
- Compatibility: iOS and Android mobile apps; Windows and Mac (browser-based)
WatchGuard AuthPoint is an intuitive, easy-to-customize authentication app that securely protects logins to corporate computers, VPNs and cloud-based apps. AuthPoint is part of WatchGuard’s broader suite of cybersecurity products, including firewalls, patch management, DNS-level protection and secure business Wi-Fi.
We love how simple the user-friendly dashboard makes it to manage AuthPoint and other WatchGuard services. Your IT team won’t waste time switching between apps, freeing them up to focus on more critical tasks. From the dashboard, you can set which verification tests users must pass when using the authenticator app and easily configure features like single sign-on (SSO). SSO enables staff to access multiple apps, like Zoom and Salesforce, with one login, eliminating the need to remember multiple passwords.
AuthPoint is a great fit for midsize companies and businesses with distributed workforces that require consistent, high-level security across their organization.
WatchGuard AuthPoint features and benefits
- Multiple authentication routes: Users can verify their identity through mobile apps, one-time codes, QR codes and even physical tokens.
- Easy setup: Quick-start wizards guide users through every step, making it easy for nontechnical staff to set up MFA apps.
- Customizable security rules: Create rules that reflect risk, such as requiring extra verification when someone logs in from an unfamiliar location or new device.
- Mobile device DNA: AuthPoint recognizes trusted mobile devices using unique identifiers, blocking attackers who try to access your system with cloned or tampered phones.
- Offline authentication: Remote and traveling employees can still access your system without an internet connection, reducing downtime and frustration.
- Great platform compatibility: AuthPoint’s app store connects with over 130 business applications, so you don’t have to hire an outside developer to integrate your tools.
Alongside MFA, many small businesses are adding
biometric authentication — including fingerprint and iris scanning — to their security systems to prevent unauthorized access.
3. LastPass Adaptive MFA
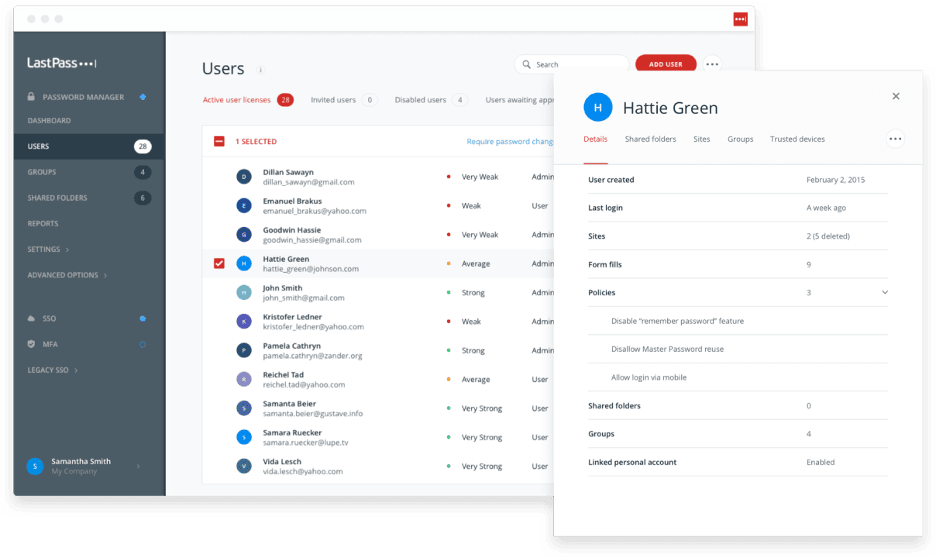
LastPass has a user-friendly interface and an intuitive control panel. Source: LastPass
- Price: Included in all LastPass plans, from Free to Business. The Business tier, which includes VPN support, on-premises MFA and passwordless MFA, costs $7 per user, per month (billed annually).
- Compatibility: iOS and Android mobile apps; web browsers; supports hardware tokens
LastPass Adaptive MFA offers a wide range of authentication options to protect your company’s internal systems, cloud network and business apps. The Adaptive MFA service is included at no extra charge for companies subscribed to a LastPass password management plan.
The platform includes the LastPass Authenticator app, which sends one-time codes and push notifications to help users log in securely. You can also enable identity verification through device-specific checks, biometrics (like fingerprint or facial recognition) and hardware security keys, such as YubiKeys or Feitian keys.
We appreciate the effort LastPass puts into user experience; the platform is accessible to both technical and nontechnical employees. We also like that it uses end-to-end encryption, keeping your data secure in transit to and from LastPass’s servers.
LastPass offers strong value if you’re looking for a full-company solution to prevent data breaches and phishing attacks. However, if you’re only seeking a dedicated MFA tool, there are more affordable options with fewer bundled features.
LastPass Adaptive MFA features and benefits
- Multistep protection: Chain together the verification methods you choose to make it as hard as possible for hackers to break in.
- Easy for employees: Whether it’s backup codes or fingerprint scans, LastPass’s authentication tools are intuitive and quick for staff to use.
- Intelligent security checks: If something seems off — like a login from a new location or at an unusual time — the LastPass Authenticator app prompts for extra identity verification.
- Extended protection: Top-tier subscribers get access to VPN, workstation and on-premises app MFA.
- Security dashboard: View a real-time snapshot of your organization’s digital security, including your LastPass security score, accounts that need action and more.
- User vaults: Each employee gets a personal security vault to store and manage their login credentials in one secure place.
4. Cisco Duo Mobile
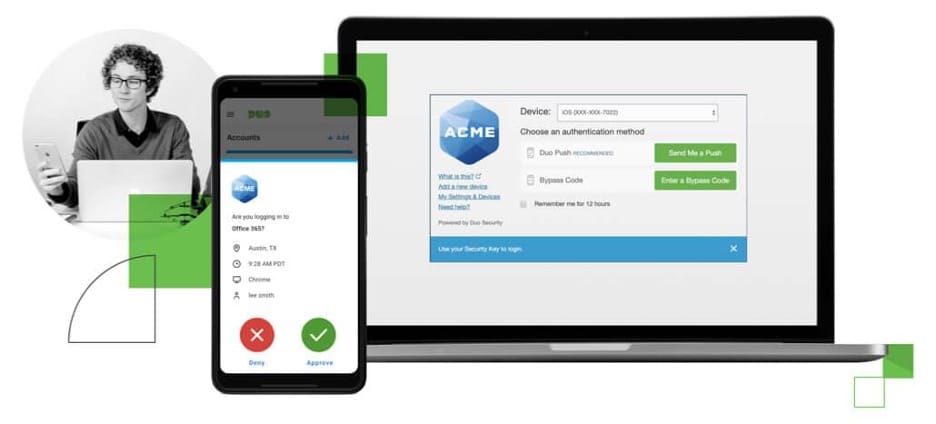
Cisco Duo is easily accessible across a variety of platforms. Source: Cisco
- Price: Free for up to 10 users; paid plans unlock more features.
- Compatibility: iOS and Android mobile apps; Windows, Mac and Linux desktop apps
Once you start using Cisco Duo, you’ll quickly learn that this vendor focuses on removing complexity from MFA. The apps download quickly and are easy to use.
The admin interface is also intuitive. This is the case whether you’re setting up a new user or choosing which verification methods employees must use to access corporate networks, cloud apps or VPNs. From the dashboard, you can monitor device security at an individual level, configure SSO policies, and enable biometric login or passwordless authentication. You’ll also see who’s logged in, what devices they’re using and whether those devices meet your company’s security requirements.
Higher-tier plans include more advanced tools like risk-based authentication, threat detection and zero-trust access. Cisco has wisely positioned its Duo platform as a strong option for businesses of all sizes seeking powerful, user-friendly MFA protection without the steep learning curve.
Cisco Duo Mobile features and benefits
- Multiple verification routes: Duo gives employees several ways to verify their identity, including the Duo Push app, SMS codes, phone callbacks and hardware keys.
- Strong phishing protection: Defend against social engineering attacks with phishing-resistant methods like FIDO2 hardware keys and Verified Duo Push.
- Adaptive security: Duo learns user behavior and prompts for additional verification when something seems off, like a login from a new location or an outdated device.
- Device audits: Check whether employee devices are running the latest operating systems and security patches. You can warn or block users who need to update.
- Range of integrations: Use Duo to secure access to cloud platforms like AWS and Azure, as well as tools like Salesforce, SAP, Zoho and HubSpot.
- Free for SMBs: Cisco’s free plan for up to 10 users includes robust MFA features and a built-in authenticator app to help you get started.
If you're
setting up an online store, be sure to build in two-factor authentication to protect your customer accounts and business data.
5. Okta Workforce Identity
Okta users can easily view the apps they have access to. Source: Okta
- Price: From $6 per user, per month. Custom pricing for larger organizations.
- Compatibility: iOS and Android mobile apps; Windows and Mac (browser-based); supports MFA hardware
Okta’s Workforce Identity platform is a highly secure option for businesses that need to protect logins for employees, contractors and strategic partners. The Okta Verify authentication app is especially powerful out of the box; it connects to over 7,000 pre-built app integrations, covering both cloud-based and on-premises software. This practice can save IT teams a significant amount of setup time.
Okta Verify supports passcodes, biometrics, push notifications, one-time passwords, and SMS and QR-based verification. One standout feature is FastPass, which can verify a trusted device and may eliminate the need for passwords entirely.
Okta is also known for its free password manager, which provides strong protection for individual accounts. But, for business use, we especially like the Workforce Identity platform, which represents a big step forward in user verification. A key advantage is adaptive MFA, which adjusts the level of verification required based on factors like user behavior, login location and device health. Organizations can also implement phishing-resistant technologies like hardware keys and smart cards as part of their MFA rollout — essential for defending against social engineering attacks.
Okta Workforce Identity is on the pricier side, but it offers a few standout capabilities, including workflow automation. For example, it can verify a customer’s identity and automatically push it to your CRM as a lead. It’s definitely worth shortlisting, though budget-conscious businesses may find better value with other platforms.
Okta Workforce Identity features and benefits
- Offline MFA backup: Team members can log in using offline passcodes when internet access is limited or unavailable.
- User directory: Store user information in a central location to streamline access and strengthen security.
- Simplified user life cycle: Automatically onboard new hires, manage permissions and remove access promptly when employees, contractors or partners leave.
- Device access management: Protect company data by limiting access to approved devices, apps and internal resources.
- Centralized user management: Manage users, groups and permissions from a single dashboard to simplify administration.
- Privileged access management: Securely control and monitor access to administrator and high-risk accounts across critical systems.
6. RSA SecurID
Get real-time analytics on all aspects of network security, including access attempts. Source: RSA
- Price: Contact the company for pricing.
- Compatibility: iOS and Android mobile apps; Windows and Mac (browser-based); supports MFA hardware
RSA SecurID offers strong protection for businesses with on-premises, hybrid and multicloud environments. Through the RSA Authenticator app, users can log in using various methods, including FIDO passkeys (mobile keys stored on smartphones or security keys); biometric verification; QR codes; one-time passcodes; code matching; and app-based push approvals.
We were impressed by the system’s intelligence. It learns user behavior and device patterns, helping reduce unnecessary login prompts while still triggering extra verification when something seems off. We also liked the platform’s strong offline capabilities and the robust support available through RSA and its global partner network.
This flexible, easy-to-use system is a smart choice for medium and large enterprises. However, the platform’s extensive feature set may be more than most SMBs need — and it may come with a higher price tag than they’re looking for.
RSA SecurID features and benefits
- Zero-trust security: SecurID verifies every login individually, continuously confirming each user’s identity as they move across systems and apps.
- Easy user management: IT teams or system admins can quickly add, monitor and remove users directly from the dashboard.
- On-premises installation option: Businesses running on-premises or hybrid environments can install the software directly on their own hardware.
- Flexible security policies: Set role-, location- and device-specific access rules to fit your organization’s needs.
- High-compliance hardware keys: RSA’s iShield Key 2 Series meets leading cryptographic standards, including FIPS 140-3, HOPT, PIV and FIDO2.