In today’s fast-changing world of business regulations and data security, many leaders face privacy and protection challenges they aren’t fully prepared to handle. Most understand the basics of encryption, but cloud encryption can seem far more complex, and with so many methods to choose from, small and midsize businesses (SMBs) often feel overwhelmed.
To simplify this critical topic, here’s what SMB owners should know about cloud encryption and how it keeps their data secure.
Editor’s note: Need a cloud storage solution for your business? Fill out the below questionnaire to have our vendor partners contact you with free information.
What is cloud encryption?
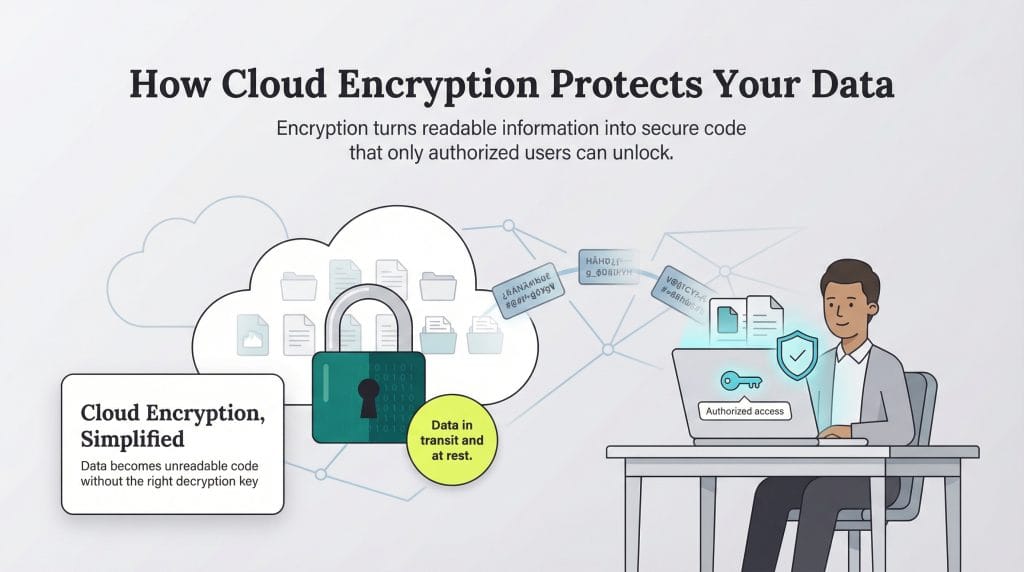
Cloud encryption is the process of protecting data used, stored or transferred through cloud computing by converting it into an unreadable format. It turns readable data into scrambled code that’s useless without the right decryption key. Even if a hacker intercepts your email or web traffic, all they’ll see is gibberish. They might have the data, but without the key, it means nothing.
When companies move operations to the cloud, they’re storing sensitive business information on infrastructure they don’t fully own or manage. That means they must rely on third parties to safeguard it. Cloud encryption fills that gap by ensuring only authorized users can access information, even if it’s intercepted or stored off-site. Whether you manage your own encryption keys or depend on your provider, it’s your strongest line of defense in a shared digital environment.
According to
Gartner, the public
cloud services market is expected to reach $1.48 trillion by 2029, up from about $723 billion in 2025. This steady rise shows how deeply cloud computing is becoming embedded in everyday business operations and why encryption remains essential for protecting critical data.
What is data protection?
Data exists in three different states: in transit, in use and at rest.
- Data in transit: Information moving from one location to another, for example, from a hard drive to a cloud server or as an email attachment sent through Slack.
- Data in use: Information that’s currently being read, processed, changed or updated on a computer system.
- Data at rest: Information stored in the cloud or on a physical or logical medium, such as a hard drive, flash drive or server.
Not all corporate data requires encryption, and not every user needs the same level of access, said Vic Winkler, a cybersecurity and information security consultant. Businesses should establish clear rules that define which data requires encryption and which can safely remain in plain text. Winkler noted that using SaaS applications with built-in encryption can greatly reduce risk while keeping critical information protected without disrupting daily operations.
Data in any state may require encryption, but protecting data at rest is particularly vital, Winkler added. The best approach is to encrypt sensitive data as soon as it’s created, ensuring that whether it’s stored in a local data center or in the cloud, it remains secure.
How does cloud encryption work?
Cloud encryption works by converting readable data into an unreadable code that only authorized users can unlock. It relies on encryption keys: unique strings of characters that act like digital locks and keys for your data. Most modern systems use the Advanced Encryption Standard (AES) with 256-bit keys, which is widely considered the gold standard for business data protection.
There are two main types of encryption: symmetric and asymmetric.
- Symmetric encryption: Uses the same key to both lock and unlock data. Symmetric encryption is fast and efficient.
- Asymmetric encryption: Uses two keys: a public key that encrypts data and a private key that decrypts it. Asymmetric encryption offers stronger security but requires more computing power.
Both encryption methods have trade-offs. Symmetric encryption is faster, while asymmetric encryption provides an extra layer of security. But regardless of the method you use, losing or destroying your encryption keys can make your data permanently inaccessible, so secure key management is essential to your cybersecurity plan.
In most cloud environments, encryption can happen at different stages
- Before data is uploaded (client-side)
- During transfer
- Once it reaches the provider’s servers (server-side)
The Cloud Security Alliance recommends the following best practices:
- Encrypting sensitive data with approved algorithms and long, random keys
- Keeping data encrypted when moving between systems
- Maintaining encryption while data is in transit, at rest and in use
Ideally, data should remain encrypted until the moment it’s needed. When it’s accessed, both the decryption keys and decrypted data should exist only briefly in a secure memory space before being re-encrypted or erased.
Not all data needs to be encrypted. Differentiating between low-risk data that can be stored in plain text and high-risk data that requires encryption helps reduce the risk of a
data breach.
Benefits of cloud encryption
Cloud encryption offers major advantages for businesses looking to protect sensitive information and strengthen trust with customers.
- Enhanced data security: According to Verizon’s 2025 Data Breach Investigations Report, ransomware was a part of 39 percent of breaches in large organizations — but was involved in a striking 88 percent of breaches in SMBs. Encrypting your data adds a critical layer of protection against unauthorized access, even if cybercriminals manage to breach your cloud storage.
- Increased collaboration: When security risks are reduced, teams and clients can share data across internal systems with more confidence. Cloud encryption supports secure access without slowing productivity, helping create more workplace collaboration.
- Regulatory compliance: Many industries now require encryption for sensitive information. Healthcare providers must meet HIPAA standards, financial institutions must comply with PCI DSS, and companies handling EU citizen data must follow GDPR regulations — all of which list encryption as a key security control.
Challenges of cloud encryption
Cloud encryption also brings challenges. Here are a few to keep in mind:
- Performance considerations: Even with modern processors designed to speed up encryption, the process still takes computing power. A 2025 Tencent Cloud analysis found that encrypting and decrypting data can significantly slow things down, especially in systems that handle large volumes or real-time transactions. It’s a good idea to run performance tests before rolling encryption out company-wide, so you can find the right balance between speed and security.
- Data loss: When encryption key information is lost, the encrypted data is lost, too. This can present various kinds of problems for projects both in the past and future.
- Implementation complexity: Managing encryption in the cloud takes planning, expertise and ongoing oversight. According to Thales’ 2025 Cloud Security Study, 57 percent of organizations now use five or more key management systems — a trend that adds cost, complexity and risk. Similarly, the Cloud Security Alliance reports that fewer than 10 percent of enterprises encrypt 80 percent or more of their cloud data, highlighting how difficult large-scale implementation can be. Building an effective key management strategy requires skilled personnel and careful coordination to avoid costly mistakes.
While cloud encryption offers many advantages, you and your team should also understand its potential challenges before adopting it as part of your organization's
cybersecurity and risk management plan.
Cloud encryption best practices
Given that cloud encryption is one of the most important security measures a business can take, here are some things to keep in mind.
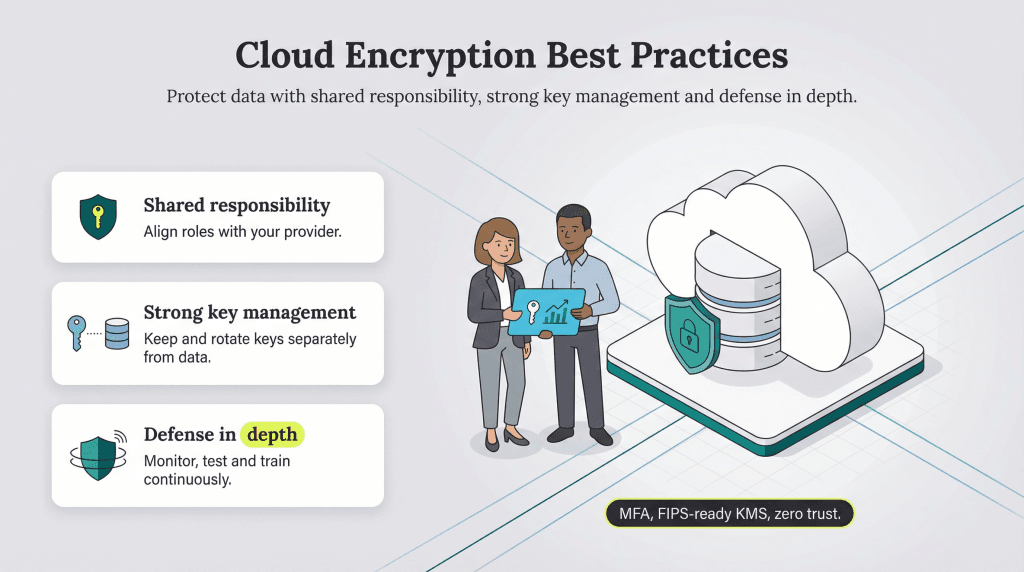
1. Treat data security as a joint venture between your company and your cloud provider.
The shared-responsibility model draws a clear line: Your cloud provider secures the infrastructure, while you’re responsible for protecting your data and access controls. Getting this balance right is critical. According to Check Point’s 2025 Cloud Security Report, 65 percent of organizations experienced at least one cloud-related security incident in the past year, many linked to misconfigured assets and identity governance gaps. These blind spots show why security in the cloud must be a partnership — one that requires vigilance on both sides.
To hold up your end of the shared-responsibility model, here are some best practices to strengthen your cloud security:
- Multifactor authentication: Strengthen account access by using phishing-resistant multifactor authentication (MFA), such as FIDO2 security keys or passkeys, instead of relying solely on SMS or app-based codes. According to research published by Microsoft, implementing MFA resulted in over 99.22 percent fewer compromises among accounts studied.
- Microsegmentation: Limiting data access based on role and usage helps contain damage if a breach occurs. For instance, a lower-level employee should have access only to the files and applications needed to do their job. If an attacker gains access through that account, the harm they can do stays confined to a small part of the network.
- Zero trust architecture: Follow a “never trust, always verify” model that continuously checks every user and transaction, whether it originates inside or outside your network. By requiring verification every step of the way, zero trust minimizes the chance of unauthorized access and strengthens your overall security posture.
Use a password manager to create and store long, unique passphrases for your encryption keys (ideally 20 characters or more). Add
multifactor authentication with an
authenticator app for extra account security, and consider hardware security modules (HSMs) for highly sensitive data.
2. Manage your encryption keys separately from your data.
Keeping encryption keys separate from the data they protect is one of the simplest and most effective ways to stay secure.
“One area we caution our healthcare clients to watch out for is the storage and use of encryption keys. They often store the keys in the same location as the data itself,” said Cortney Thompson, chief information officer of data center and managed services provider Lunavi. “If your data is compromised, your key would be too — which is why it’s more secure to keep them separate.”
Best practices for key management include:
- Automating key rotation every 90 days
- Maintaining encrypted backups in geographically separate locations
- Using key management services (KMS) that support FIPS 140-2 Level 3 validation
- Establishing “break-glass procedures” for emergency key recovery
- Maintaining detailed audit logs of all key access events
- Giving master and recovery keys multifactor authentication
Thompson also noted that encryption keys must be refreshed regularly. “This is often forced on companies as the key itself is set to expire automatically, but other keys need a defined refresh schedule,” Thompson explained.
Manny Landrón, CISO of Enact Mortgage Insurance, noted that in some cases, it may be better for cloud service providers or third-party proxy providers to manage a company’s encryption keys instead of the internal IT team. This approach can prevent issues that arise when encrypted data is uploaded to the cloud but the decryption key isn’t accessible to remote or mobile devices — or when sharing data with business partners who shouldn’t have direct access to the keys.
A third-party provider can add another layer of protection by keeping keys separate from the encrypted data stored in the cloud. However, this setup isn’t right for every business; it can add complexity and cost, especially for smaller organizations.
3. Don’t become entirely reliant on cloud providers.
Partnering with a cloud service provider (CSP) to encrypt your data and manage your keys is smart. However, no one will care about your data as much as you do. If your company experiences a breach, customers and the press won’t blame your CSP: They’ll hold your business accountable.
Recent regulations make that responsibility even clearer. The SEC’s cybersecurity disclosure rules require public companies to report material breaches within four business days of determining an incident is material, even if it occurs at a third-party provider. While small businesses aren’t directly covered by SEC mandates, many face similar disclosure obligations under state laws and industry-specific regulations.
That’s why a defense-in-depth strategy is essential:
- Maintain an incident response plan that specifically addresses cloud breaches.
- Conduct quarterly security assessments of your configurations.
- Provide ongoing security awareness training for your team.
The Cloud Security Alliance recommends continuous monitoring and automated compliance checks to maintain full visibility into your cloud environment. It also cautions that cloud providers — and their employees — should never have access to your decryption keys.
“This stipulation can be the most challenging for SMBs, depending on their use of cloud,” cautioned Jeff Cherrington, principal at NextGen Product Management Consulting. “For simple file sharing, there are some good add-ons for Dropbox and similar offerings. When an SMB moves processing to the cloud, things become a bit more complex.”
The best cloud services on the market
With cybersecurity incidents costing U.S. businesses an average of $4.4 million, according to IBM’s Cost of a Data Breach Report, data security should be at the top of your priority list. When evaluating cloud services, look for providers that offer end-to-end encryption, comply with SOC 2 Type II standards, and provide transparent security documentation.
Top options to consider include:
- IDrive: AES 256-bit encryption with HIPAA compliance for healthcare organizations.
- Egnyte: Zero-knowledge encryption and granular access controls for enterprise environments.
- Backblaze: Client-side encryption and immutable backups to guard against ransomware attacks.
For large-scale deployments, Microsoft Azure and Amazon Web Services (AWS) remain leading choices for enterprise-grade infrastructure.
Beyond choosing the right provider, make sure your internal policies match your technology. Establish clear cloud access protocols, enable multifactor authentication, and take advantage of built-in encryption tools in the software your teams already use. Schedule regular cybersecurity risk assessments to identify gaps and ensure your protections evolve with new threats.
Source interviews were conducted for a previous version of this article.