IT Management
Whatever hardware, software and networks your business relies on needs to be managed. But whether you have a single IT administrator or a full in-house tech support team, our guides and resources can help you make the right moves when it comes to internet service, cybersecurity, remote access, storage and more.

PowerShell modules allow you to combine multiple scripts to simplify code management. Learn step-by-step instructions for creating and using these modules.

Businesses base decisions on their current and future data. To steer a company in the right direction, leaders should maintain data integrity.

Learn how your business can benefit from digital asset management, which will boost productivity, improve collaboration, and save time and money.
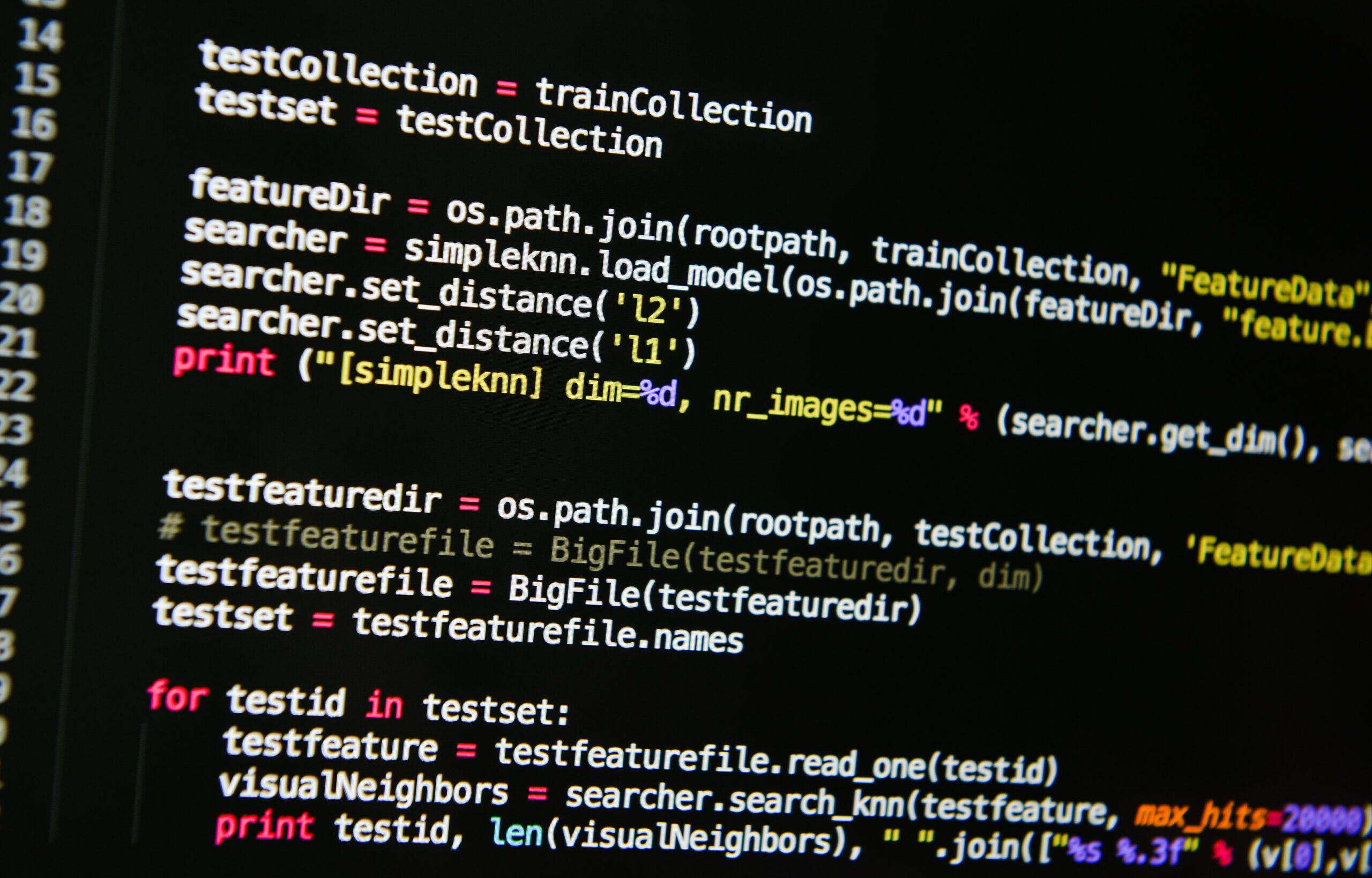
While software can sync files and folders for you, it's often limited in scope. Learn how a PowerShell script can help you build a custom solution.

Although native support for Secure File Transfer Protocol (SFTP) is not in PowerShell, by using a free module, you can retrieve, delete and add new files.

Connecting to any device over the internet, as you would through remote PC software, has risks. Follow these practices to access remote PCs securely.

Web scraping tools gather a website's pertinent information for you to peruse or download. Learn how to create your own web scraping tool in PowerShell.

Managing Windows user profiles is often time-consuming and tedious. Here are some tips on how to leverage PowerShell to make the process easier.

PowerShell helps IT experts manage IIS web server farms with dozens or hundreds of app pools. Learn how to manage IIS application pools with PowerShell.

What is PowerShell? Microsoft PowerShell is a powerful administrative tool that can help you automate tasks for your computer and network.

Zoom Phone offers internet-based phone services with feature-rich video conferencing tools. See pricing and how it stacks up to competitors.

Here's how to find an effective, affordable security system for your business.

Claim scrubbing is the process of verifying that a medical claim's codes are accurate. Learn how code scrubbing works and which tools can help.

Learn eight ways to improve your bottom line and create a more sustainable business environment by using practices such as cloud-based computing.
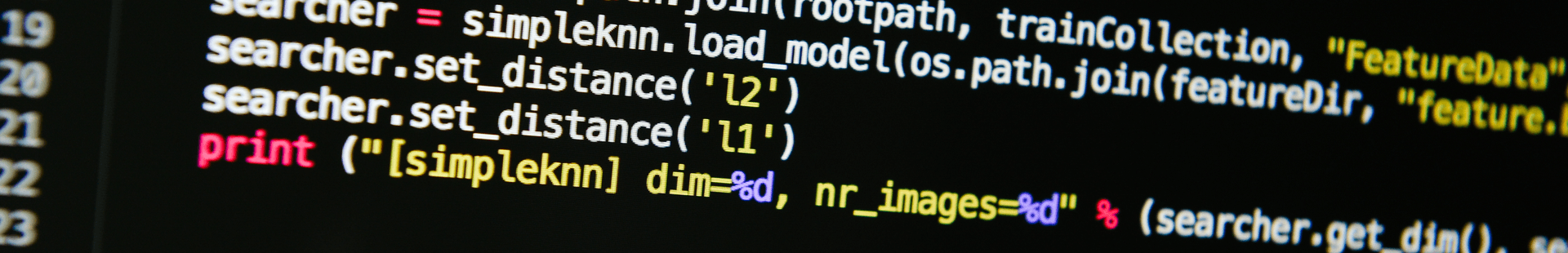
Before you can change an ACL, you must get the current one. There are two ways to do this with PowerShell. Learn how to get the current ACL and modify it.

Every Wi-Fi user appreciates a faster connection. The IEEE 802.11ax draft standard promises better range, throughput and resiliency.

RFID (radio frequency identification) can identify and track inventory. Learn how RFID is used in retail and what you need to know to use it effectively.

It can be challenging to keep your digital documents organized and safe. These 10 file management practices will help you get started.

The cloud can help your business grow. Learn what the cloud is, the benefits of cloud services and software, and how much cloud services cost.
Find out everything you need to know about cloud encryption, encryption keys and best practices to protect your data.

Need an internet service provider for your business? We've researched and analyzed the top providers to help you find the one that's right for you.
Learn what cybercrime is and how to prevent it. Protect your business from phishing, ransomware and other attacks with proven cybercrime protection strategies.

Businesses must convince customers their personal data is safe. Run a cybersecurity risk assessment to protect company and customer data.

You can use PowerShell with Windows Software Update Services to work with servers and Windows clients.

Check out our six-step process to create an effective remote help desk for your business and see recommended software.

Small businesses spend 13.2% of IT budgets on cybersecurity. Experts suggest focusing on employee training, MFA,and practical defenses over costly tech.

Being online is essential to conduct business, and in our helpful guide, we’ll show you how to find the right business internet service provider.

This guide explains business broadband, how it works and the ways businesses can use it to their advantage.

Business DSL or cable internet: Which is the right choice for your business? Read on to learn more about each option and reputable providers.

Not all applications are created with remote execution in mind. PowerShell provides several ways to invoke applications on remote computers.