Table of Contents
As technology advances, internet bot activity — both good and bad — is growing. Unfortunately, advanced bots have made it easier for fraudsters to commit crimes. According to the 2024 Imperva Bad Bot Report, almost a third of all internet traffic was attributable to bad bots.
Since bot traffic affects many verticals, small and midsize businesses (SMBs) need to understand the potential threats posed by bots. Here’s a look at bot-driven credit card testing fraud, how these attacks work and how you can protect your business and customers from this e-commerce threat.
How do bots work?
A bot is an automated program that mimics human activity, according to Dr. Arun Vishwanath, author of “The Weakest Link.” “Think of it as a tireless worker executing tasks at lightning speed — whether it’s logging into accounts, spamming emails or gaming systems to commit fraud. Unlike humans, bots don’t tire, hesitate or make mistakes, which makes them formidable,” he said.
Bots often target online retailers by testing stolen credit cards with small purchases at odd hours, such as midnight, he explained. “Businesses might also notice unusual spikes in transactions — bulk purchases right before a sale or patterns that don’t match typical customer behavior,” added Vishwanath. “These are red flags. Spotting bots is a game of vigilance and pattern recognition, but tools like fraud detection software can help even the odds.”
What is credit card testing?
Credit card testing fraud, also known as carding and card cracking, is when cybercriminals make a small online purchase to test whether a stolen credit card number is valid.
Credit card testing often goes unnoticed by fraud detection solutions and is usually discovered only when it’s too late. Without proper measurements in place, credit card testing fraud can be costly and damaging to both SMBs and cardholders.
How does a credit card testing attack work?
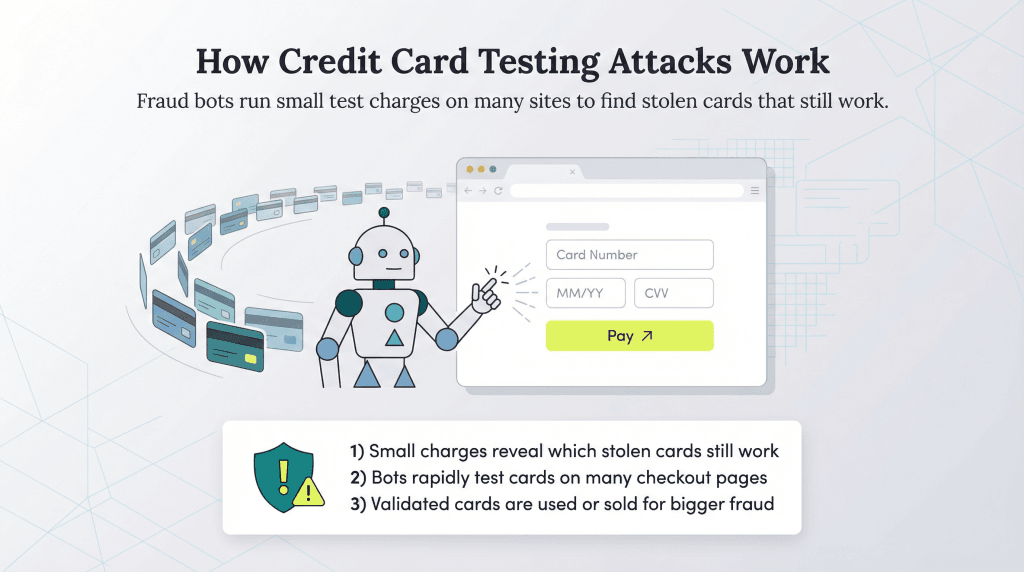
Fraudsters can potentially abuse any user-related function on your company’s website, such as the ability to enable payments. Once the scammer purchases a list of stolen credit card numbers, they test them to see which ones are valid by making small transactions on unsuspecting e-commerce sites.
Fraudsters can enable bots to do this work efficiently. A bot can submit orders on multiple websites automatically to check credit card validity much faster than a fraudster inputting card numbers one by one could.
The fraudster’s end goal is to find valid credit cards they can use to make large online purchases or sell the list of validated credit cards to other cybercriminals.
Example of a carding attack
In 2019, a carding bot called the Canary Bot was discovered by PerimeterX, a provider of solutions designed to curb online fraud. The Canary Bot was designed to target e-commerce platforms. Mimicking a real shopper, the bot added products to an online shopping cart, set shipping information and completed the sale on multiple businesses within the platform.
The bot was discovered because its pattern differed from that of human shoppers. For example, activity increased before the holiday shopping season, which isn’t typical, since people usually wait for sales. The bot’s transactions also didn’t follow the usual human shopping time patterns; instead, the transactions happened randomly throughout the day.
What are the ramifications of credit card testing for small businesses?
Bot-driven credit card testing hurts SMBs with chargebacks, shipped goods that are never recovered, lost revenue from fraudulent sales and rising operational costs. After all, getting to the bottom of higher decline rates or failed transactions takes up precious time — and may distract customer service staff from more important day-to-day activities. It also hinders analyzing corporate data, obscuring the genuine customer numbers and potentially distorting real growth levels.
Damage to your brand reputation may occur, especially if you end up caught in the middle of credit card fraud warnings or payment disputes between a consumer and their credit card provider. Your reputation may be harmed in other ways, too — if your business unintentionally allows one fraudster to enter the networks, other cybercriminals might follow. Plus, higher decline rates can make your transactions seem riskier to card issuers/networks, potentially leading to legitimate transactions being queried or blocked more frequently.
How do fraudsters get a person’s credit card number?
In the age of security breaches and hacks, data centers and credit card agencies unintentionally give hackers abundant access to credit card numbers. Typically, hackers sell a bulk list of stolen card numbers on the dark web, where a buyer — the fraudster — is lurking.
A fraudster can purchase lists of credit card numbers; the list’s resale value depreciates over time. Many cardholders and banks take preemptive measures to shut down credit cards if there is a breach, but a small, unauthorized purchase may go unnoticed.
How do you identify credit card fraud?
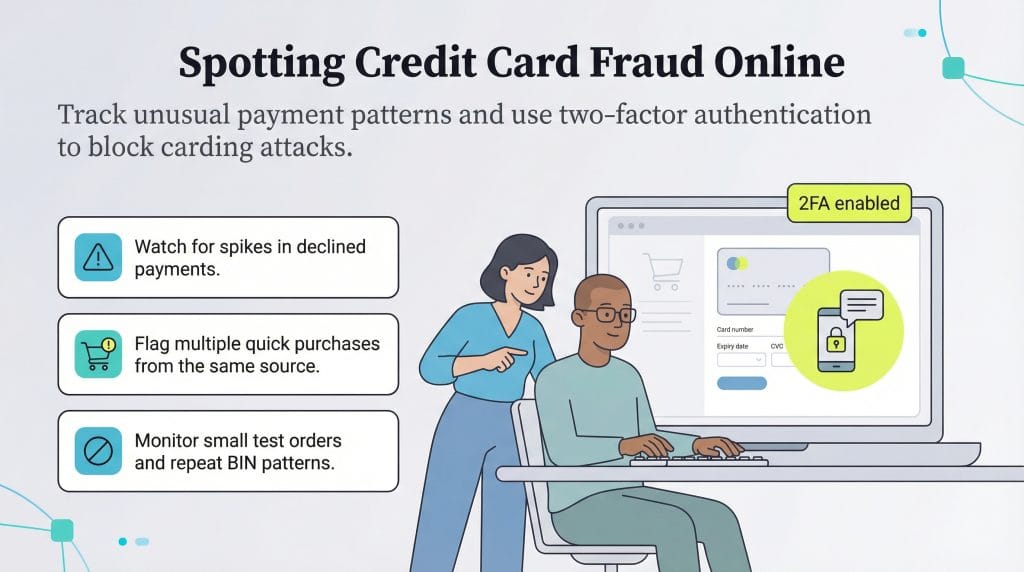
Luckily, you can spot red flags when carding attacks occur. Here are some things to look for:
- Unusually high shopping cart abandonment rates and chargebacks
- Small shopping cart sales
- High proportion of declined payments
- Disproportionate use of the payment step in the shopping cart
- Multiple payments from the same customer within seconds or minutes
- Too many transactions with the same bank identification number, which is the first six digits of every credit and debit card
- Multiple declined transactions from the same user, internet protocol (IP) address or session
How can you protect your business from credit card fraud?

While both large and small businesses face increasing credit card fraud, SMBs are potentially more vulnerable since they often have fewer protections in place and less knowledge about current attacks, according to Brittany Allen, senior trust and safety architect at Sift. “One of the most important things you can do for your business is to implement strong, AI-powered fraud detection tools, which use machine learning to identify and block suspicious transactions,” she advised. “With the speed, sophistication, automation and scale of today’s fraud attacks, businesses won’t be able to keep up unless they have the right technology in place.”
Robust fraud prevention technologies can identify these patterns quickly, explained Allen. For example, pinpointing transactions at odd hours since bots frequently operate when human activity is low. “Other signals include a high velocity of failed transactions or unusual purchasing patterns, such as small, frequent purchases,” she said.
If you’re a small business owner, these are some of the key recommendations to mitigate the risks of credit card fraud:
- Scrutinize historical operational trends: Increased customer support calls and chargebacks could mean card testers are targeting you. Also, look for spikes in the number of declined transactions. When fraudsters test older stolen credit card lists, many declines will occur.
- Install automated blocking software: Most engineering teams can use simple blocking software for high-velocity attacks, but more sophisticated attacks need dedicated software. Some vendors specialize in this type of real-time fraud detection. Make sure your solution can quickly adjust to changing attack patterns and deliver obfuscation strategies to make it harder for fraudsters to complete a sale.
- Partner with a secure payment processor: The best credit card processing services have strong fraud and risk management engines with bot protection. Integrating with the right partner allows you to collect payments and focus on your business with peace of mind.
- Utilize device fingerprinting: This technology combines data from the user’s browser and device to identify a source. Because carding involves multiple attempts and the fraudsters have limited devices at their disposal, fingerprinting can identify the source of carding attacks and shut them down.
- Enable browser validation: Bots hide their tracks by pretending to run a certain browser and then using multiple user accounts. Browser validation analyzes the browser’s JavaScript and activity to ensure that an account acts like an actual human.
- Familiarize yourself with purchasing patterns: Human behavior and purchasing habits conform to specific patterns, including URLs, mouse movements and site engagement. When behavior deviates from the norm, it’s a red flag that a bot may be involved.
- Analyze your traffic: There are certain technical and behavioral patterns common to bots and specific IPs where they tend to originate. By keeping a keen eye on your traffic patterns, you may be able to nip a carding attack in the bud.
- Use address verification service (AVS) responses. An AVS matches the billing address input at checkout with the address on file with the credit card company. If it doesn’t match, the credit card company will still let the transaction go through, but you can set safeguards or use other fraud prevention tools to research the matter.
- Require card security codes: When companies store credit card information, they can’t store the comma-separated values or card verification value codes and cybercriminals will typically not have this information. By requiring the code at checkout, you can ward off criminals.
- Challenge your purchasers: You are probably aware of the many “prove you’re not a robot” challenges online, like checking a box, typing in a captcha or identifying images with a specific item. These measures prevent bots from proceeding.
- Follow established systems: Small businesses must set clear policies for their employees and explain what can go wrong if those policies are ignored. “The use of secure payment gateways that comply with industry standards and regulations are essential for safe transactions, as they often include some degree of built-in fraud detection,” added Allen.
Neil Cumins and Jennifer Dublino contributed to this article.






