Technology
It's impossible to a run a modern business without technology services. Our technology hub will guide you toward the software and tools necessary not just for everyday operations but also cost efficiency and long-term growth. Get recommendations for cutting-edge platforms, learn about the rise of AI-powered tech and find out what solutions can help you take your business to the next level.
Expert Advice, Tips and Resources for Upgrading Your Business Tech
The Best Technology Solutions for Your Growing Business


Trending Articles for Maintaining Your Business





Latest Small Business Technology Tips, Trends and Advice
Hackers target companies that rely on passwords to protect their IT systems. Learn how authenticator apps work to stop hackers in their tracks.

Ooma Office offers cloud-based VoIP phone service starting at $19.95/user/month with transparent pricing, no contracts and setup ideal for small businesses.

PowerShell modules allow you to combine multiple scripts to simplify code management. Learn step-by-step instructions for creating and using these modules.

Businesses base decisions on their current and future data. To steer a company in the right direction, leaders should maintain data integrity.

Learn how your business can benefit from digital asset management, which will boost productivity, improve collaboration, and save time and money.
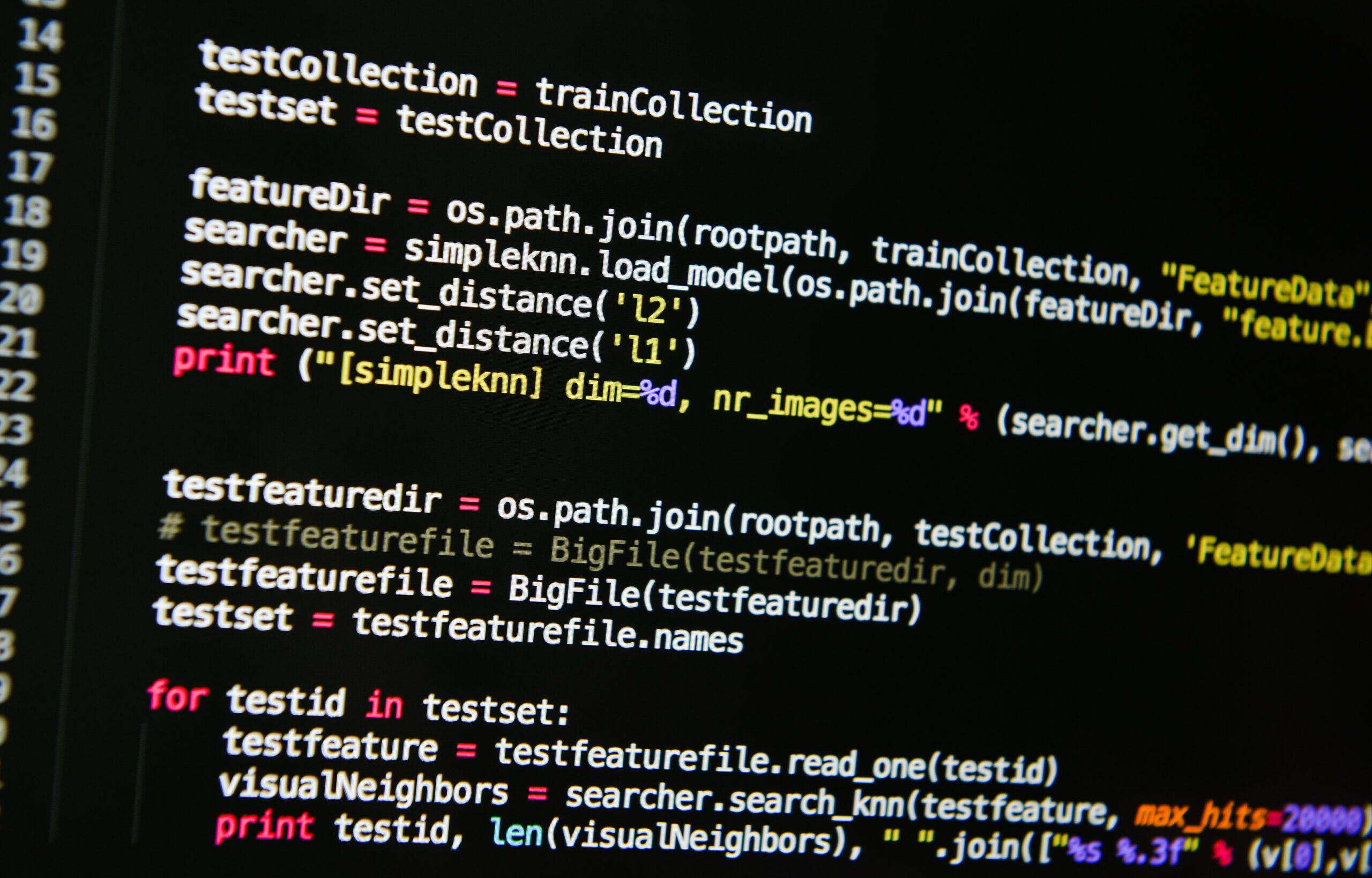
While software can sync files and folders for you, it's often limited in scope. Learn how a PowerShell script can help you build a custom solution.

The cost for software development depends on a variety of different factors. Learn how to make the right choices for your business.

Although native support for Secure File Transfer Protocol (SFTP) is not in PowerShell, by using a free module, you can retrieve, delete and add new files.

With built-in technology such as tracking tools, sensors and more, smart helmets can improve your construction team's safety, productivity and efficiency.

Video calls are integral to business communication. Learn video conference call tips and discover the best business phone systems for video conferencing.

Connecting to any device over the internet, as you would through remote PC software, has risks. Follow these practices to access remote PCs securely.

Web scraping tools gather a website's pertinent information for you to peruse or download. Learn how to create your own web scraping tool in PowerShell.

Managing Windows user profiles is often time-consuming and tedious. Here are some tips on how to leverage PowerShell to make the process easier.

PowerShell helps IT experts manage IIS web server farms with dozens or hundreds of app pools. Learn how to manage IIS application pools with PowerShell.
Technology enhances workplace communication through tools like Slack, Zoom, and email, but must balance face-to-face interactions for effective collaboration.

What is PowerShell? Microsoft PowerShell is a powerful administrative tool that can help you automate tasks for your computer and network.

Test out one of these video conferencing platforms the next time you need to host a meeting.

Zoom Phone offers internet-based phone services with feature-rich video conferencing tools. See pricing and how it stacks up to competitors.

GPS Trackit is a cost-effective fleet tracking platform with leading video telematics capabilities. See pricing and more key details.

Teletrac Navman offers useful features for staying on top of fleet maintenance, reducing long-term repair costs and keeping your vehicles operational.

Azuga stands out in the fleet tracking space for its high usability. Learn about features, pricing and more.

ClearPathGPS is a great fleet tracking system for budget-conscious businesses. See its features, plans and prices.

Samsara's GPS fleet management platform is intuitive, fully featured and ideal for companies wanting to start their transition to electric vehicles.

Verizon Connect provides a wide selection of GPS fleet tracking services that are scalable to meet the needs of any fleet size.

Automating manual processes improves efficiency and eliminates human error. Learn about workflow automation and how to create an automated workflow.

Video conferences can be effective virtual meetings or a waste of time and resources. Learn 18 tips for more productive and enjoyable video conferences.

Unstable audio or video connections can make hosting a meeting difficult for any business. Here are the most common problems and their solutions.

Here's how to find an effective, affordable security system for your business.

EHRs are a vital way to automate and streamline the healthcare process, but implementation can be challenging. Learn how to smooth the transition.

Claim scrubbing is the process of verifying that a medical claim's codes are accurate. Learn how code scrubbing works and which tools can help.